
Building Secure Access at Scale: From Identity Management to Audit Readiness
Secure access to systems, data, and applications is a cornerstone of any resilient digital enterprise. At Solid Logix, we specialize in designing and implementing comprehensive security solutions that protect sensitive digital assets while streamlining user access across private and government sector environments.

The Stakes Are High
The financial impact of poor identity management is measurable and significant, but entirely preventable with the right strategic approach.
- of data breaches involve compromised credentials
- 81%
- average cost of a healthcare data breach per incident
- $10.93M
- annual productivity loss for 15,000-employee organizations
- $5.2M
- average cost of a password reset in help desk time
- $70
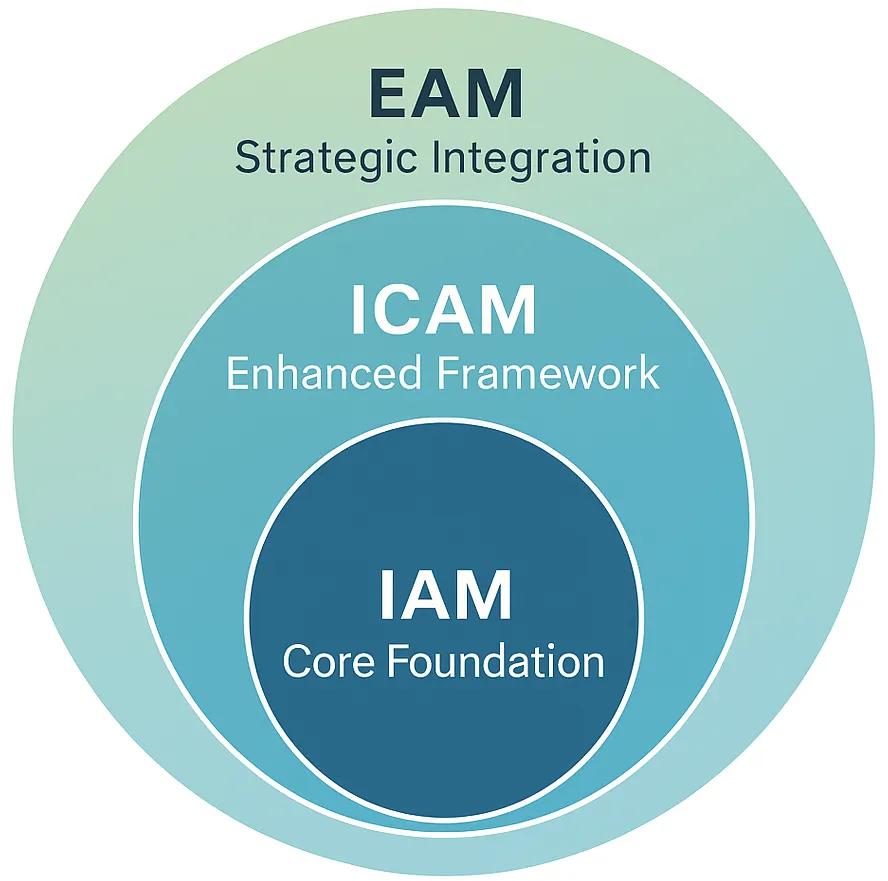
Identity and Access Management. Enterprise-Ready.
Think of your organization's digital systems like a secure office building. Just as you need to know who's entering your building and what rooms they can access, your digital environment needs the same level of control and visibility.
Identity and Access Management (IAM) is your digital front door. It serves as the foundational security layer that governs how identities are verified, authenticated, and authorized across your organization's technology stack.
IAM is your digital security system that answers three critical questions:
- →Who is trying to access your systems?
- →What are they allowed to do?
- →When and where should they have access?
At Solid Logix, we provide comprehensive identity solutions that protect your organization while making it easy for authorized users to do their jobs. We implement comprehensive identity management solutions that serve as the foundation for your organization's security architecture. Our services encompass everything from directory integration and identity federation to custom identity provisioning workflows tailored to your business processes.
Going Beyond IAM: Advanced Frameworks for Complex Requirements
IAM provides essential identity and access controls, but organizations with specific regulatory, compliance, or operational requirements need enhanced frameworks. Solid Logix helps you extend your identity strategy through ICAM and EAM for comprehensive governance and strategic alignment.
Identity, Credentialing, and Access Management (ICAM)
ICAM delivers policy-driven governance with credential-based security and risk-aware access control aligned to federal identity standards such as FICAM and NIST.
- →Enhanced credential lifecycle management with PKI integration
- →Risk based access decisions using contextual factors (role, location, device, behavior)
- →Policy driven authentication and authorization
- →Comprehensive audit logging for compliance with FICAM, HIPAA, and federal requirements
- →Integrated management of digital certificates and identity proofing
Most relevant for organizations working with federal government, defense contractors, healthcare systems requiring HIPAA compliance, and entities needing alignment with federal identity standards.
Enterprise Access Management (EAM)
EAM provides a unified approach to managing access across distributed systems, cloud platforms, and organizational boundaries while supporting business agility.
- →Centralized policy management across multiple business units and subsidiaries
- →Cross domain federation for seamless partner and vendor access
- →Delegated access management within business-defined boundaries
- →Enterprise wide access analytics and risk assessment
- →Integration with business processes and strategic IT initiatives
Most relevant for large enterprises with complex organizational structures, multi subsidiary corporations, organizations with extensive partner ecosystems, and companies managing multiple business units or geographic regions
Our Track Record
Identity Solutions We've Delivered
Real implementations across enterprise healthcare and federal agencies. Our expertise spans foundational architecture, complex integrations, and ongoing modernization for organizations with millions of users and critical security needs.
Healthcare Identity Platform Foundation
Solid Foundation • Core Architecture • Millions of Users
Our identity journey began with Imprivata, where we played a pivotal role in designing and implementing the core architecture of their healthcare identity platform. While working with Imprivata, we authored critical components that enabled secure, seamless access to clinical systems for millions of healthcare professionals. This foundational work established robust authentication, streamlined user provisioning, and set the standard for secure workflows in hospitals and clinics worldwide.
Legacy Platform FoundationEnterprise Healthcare ICAM Implementation
27 Companies Unified • Rapid Integration • Full ICAM Stack
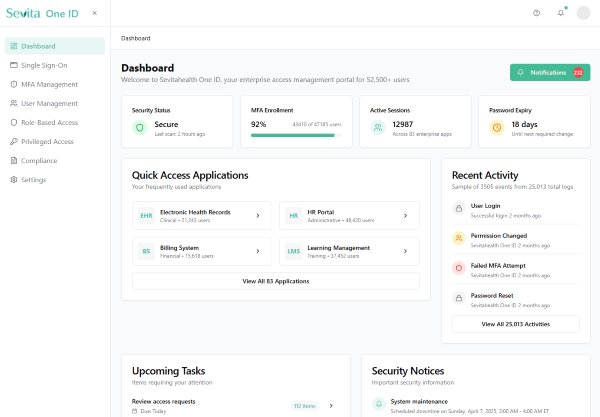
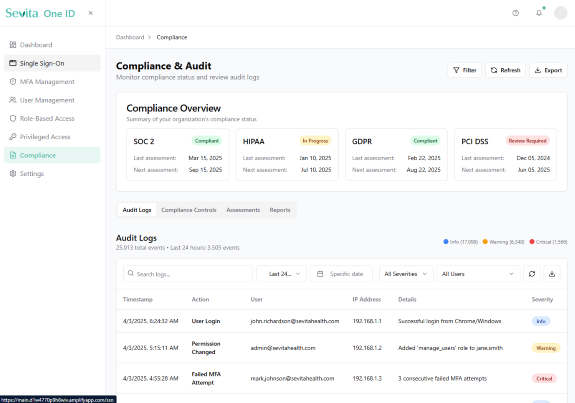
Sevita Health rapidly acquired 27 companies in just 15 months, resulting in a complex landscape of disparate identity systems and processes. We were brought in to architect and deliver a comprehensive Identity, Credential, and Access Management (ICAM) solution that unified these organizations into a single, secure ecosystem. In less than a year, we integrated dozens of systems, automated user lifecycle management, and established centralized governance. The result: streamlined onboarding, enhanced compliance, and audit-ready security controls that protect millions of sensitive health records and support ongoing organizational growth.
View Full Case StudyFederal Healthcare Access Modernization
CEAMS to CICAM Evolution • $47M Prime Recompete • Key Subcontractor Role
We are proud to support Alcor, the prime contract holder for the Centers for Medicare & Medicaid Services (CMS), in their ongoing federal healthcare access modernization efforts. For years, our team has partnered closely with Alcor to deliver critical subcontractor support, helping advance the evolution of the CMS Enterprise Access Management System (CEAMS) into the Identity, Credential, and Access Management (CICAM) platform. This long-standing collaboration recently continued with Alcor’s successful recompete award valued at approximately $47M, a testament to the strength and effectiveness of the combined team. Through our contributions, we are enabling secure, scalable access for thousands of users, reinforcing CMS’s mission to protect sensitive healthcare data while streamlining access for providers and beneficiaries nationwide.
Implementation Summary Coming SoonCritical Infrastructure Database Security
CWMS Authorization • Contract Awarded • Active Development
We are currently engaged with the U.S. Army Corps of Engineers to modernize database authorization for the Corps Water Management System (CWMS), a mission-critical platform supporting flood control, navigation, and water resource management nationwide. Our work involves designing and implementing advanced access controls, integrating with federal identity standards, and ensuring real-time authorization for sensitive operational data. By collaborating closely with stakeholders, we are strengthening compliance, reducing risk, and enabling secure, auditable access for authorized personnel. This modernization effort is vital for protecting critical infrastructure and supporting the Corps’ mission to safeguard communities and resources across the country.
Project Details Upon CompletionReady to join our roster of successful identity modernization projects? Let’s discuss how we can help you achieve secure, scalable, and compliant access management tailored to your organization’s needs.
Discuss Your ProjectAdvanced Identity Management Components
Building on the core functions of IAM, these advanced capabilities transform identity management from basic access control into a strategic security advantage, enabling precise authorization, automated compliance, and adaptive protection against evolving threats.

Feature Details
Fine-Grained Authorization
Precision Access Controls & Authorization- Role-Based Access Control (RBAC) Traditional RBAC assigns permissions based on predefined organizational roles. Users inherit access rights through role assignments, creating scalable permission management aligned with job functions and organizational hierarchy.
Attribute-Based Access Control (ABAC) Next-generation ABAC evaluates multiple attributes—user characteristics, resource properties, environmental conditions, and contextual factors—to make dynamic access decisions in real time.
Compliance & Risk Management
Identity Governance & Lifecycle Management- Privileged Access Management (PAM) Specialized controls for high-privilege accounts including shared administrative credentials, service accounts, and emergency access. Features just-in-time access, session recording, and automated credential rotation.
Identity Governance & Administration (IGA) Comprehensive lifecycle management from user provisioning through deprovisioning, including automated role mining, access reviews, certification campaigns, and compliance reporting.
Intelligent Security Operations
Zero Trust Architecture Components- Continuous Authentication & Risk Assessment Behavioral analytics and machine learning algorithms that continuously evaluate user behavior, device posture, network conditions, and access patterns to dynamically adjust authentication requirements.
Just-in-Time (JIT) Access Provisioning Temporary access grants based on specific requests, business justification, and time-bounded approvals. Eliminates standing privileges and reduces attack surface through principle of least privilege.
Credentials Management
Multifactor Identity Assurance- Once a user’s identity is established, credentials provide a way to prove it—again and again. These may include PIV cards, biometrics, mobile authenticators, or digital certificates. Passwords alone are no longer sufficient.
Effective credentials management supports issuance, renewal, revocation, and integration with both cloud-native and legacy authentication frameworks.
Identity Lifecycle Automation
Provisioning and Deprovisioning at Scale- Provisioning systems automatically assign access and create accounts as users join an organization, move roles, or change departments. This includes permissions, group memberships, and communications access.
On departure, deprovisioning workflows shut down accounts, revoke roles, and remove credentials across systems to reduce insider threats and ensure compliance.
Federated Identity
Reuse and Trust Across Boundaries- Federation allows users to log in once and use the same identity to access systems across organizational or cloud boundaries. Common standards include SAML, OIDC, and SCIM.
This approach reduces identity duplication, supports centralized governance, and enables modern distributed architectures to function securely.
Access Request and Approval Workflows
Delegated Authorization and Review- Some access must be requested and explicitly approved. Access request systems allow users to search for what they need and submit justifications. These are routed to appropriate reviewers—managers, data owners, or security leads—for a decision.
Every step is logged, auditable, and enforceable via policy. This structure promotes accountability and aligns with separation of duties and compliance mandates.
Enterprise IAM reference architecture and strategic framework
Modern Identity and Access Management Framework
| Governance | OversightProcesses & proceduresStandards & policiesCompliance |
| Identity Lifecycle | CreateVerifyAuthenticateAuthorizeMonitor UpdateRotateSuspendArchive Technologies:Okta, Microsoft Entra, Auth0, Ping Identity, CyberArk, SailPoint |
| Access Management & Zero Trust | Request & ApproveProvision & DeprovisionEnforce & AuthorizeReview & CertifyMonitor & ReconcileAnalytics & Insights Technologies:ServiceNow, SailPoint, Saviynt, ForgeRock, BeyondTrust, Palo Alto Prisma |
| Data Sources & Integration | HRIS SystemsDirectory ServicesCloud Identity ProvidersIdentity WarehouseAsset ManagementThird-party APIs Technologies:Workday, SAP SuccessFactors, Microsoft AD, Salesforce, Google Workspace, Oracle HCM |
Built for Identity. Powered by Proven Tools.
We design and implement secure, scalable identity systems using today’s most trusted platforms. From access governance to federated identity and zero trust architecture, we know the technologies that matter, and how to use them effectively.

Why Solid Logix?
We have successfully implemented identity and access solutions across multiple large-scale enterprise environments. Our team brings deep experience and proven results from doing this many times, in both public and private sectors.
Dual Sector Experience
We have designed and implemented ICAM solutions across government agencies and commercial enterprises, giving us a wide lens into real world identity management needs.
Compliance First Design
Our platforms are built to align with frameworks like FICAM, HIPAA, and CDM, ensuring systems meet the highest federal and industry standards.
Scalability and Automation
By using role intelligence, analytics, and platform native tooling, we streamline access and simplify identity workflows at scale.
Track Record of Success
From CMS.gov to Sevita Health, our solutions have consistently cut costs, reduced onboarding time, and improved access governance outcomes.
Zero Trust, Zero Compromise
Let’s Recap: Your Path to Enterprise Access Maturity
Access Velocity
Real time identity decisions at enterprise scale
Solid Logix designs access platforms that scale with the organization. Whether serving fifty or fifty million users, our systems ensure that identity changes such as hiring, transfers, and separation are reflected across applications without delay. This supports security, speeds up onboarding, and reduces administrative overhead.
Seamless Delivery
Policy driven workflows that move at the speed of mission need
Our access delivery process integrates tightly with enterprise workflows. From account creation to privilege adjustments, each action is governed by rules that reflect business and compliance requirements. This creates a fast moving, low risk environment where security and productivity reinforce each other.
Your Security Foundation
Identity and Access Management (IAM)
Identity and Access Management forms the cornerstone of modern enterprise security. Our IAM solutions ensure that the right people have the right access to the right resources at the right time, while maintaining detailed audit trails and enforcing your organization's security policies.
User Lifecycle Management: Automated provisioning and deprovisioning as employees join, move within, or leave your organization.
Single Sign-On (SSO): Streamlined access to multiple applications with one set of credentials, improving both security and user experience.
Multi-Factor Authentication (MFA): Layered security that goes beyond passwords to verify user identity.
Role-Based Access Control (RBAC): Permissions assigned based on job functions, ensuring principle of least privilege.
Password Management: Secure password policies, self-service reset capabilities, and credential vaulting.
Government-Grade Security for Enterprise
Identity, Credential, and Access Management (ICAM)
Building on IAM foundations, our ICAM approach incorporates the rigorous standards developed for federal agencies and applies them to enterprise environments. This comprehensive framework addresses not just access control, but the entire lifecycle of digital identities and credentials.
Identity Governance: Centralized policies for identity creation, management, and retirement across all systems.
Credential Management: Secure issuance, maintenance, and revocation of digital certificates, smart cards, and other authentication tokens.
Privileged Access Management (PAM): Specialized controls for administrative and high-privilege accounts.
Federation Services: Secure identity sharing across organizational boundaries and cloud services.
Continuous Monitoring: Real-time assessment of access patterns and anomaly detection.
The Strategic Integration
Enterprise Access Management (EAM)
Enterprise Access Management represents the evolution of access control into a strategic business enabler. EAM integrates IAM and ICAM principles with broader business processes, ensuring that access management supports rather than hinders organizational objectives.
Business Process Integration: Access controls that align with organizational workflows and approval processes.
Scalable Architecture: Solutions that grow with your business and adapt to new technologies.
Compliance Automation: Built-in support for SOX, HIPAA, PCI-DSS, GDPR, and other regulatory requirements.
Analytics and Insights: Comprehensive reporting on access patterns, compliance status, and security metrics.
Cloud-First Design: Native support for hybrid and multi-cloud environments.